The latest updates Microsoft Windows Server 2012 70-411 dumps, 70-411 pdf free download, 70-411 exam practice test questions to improve your skills. “Administering Windows Server 2012” 70-411 Exam. Easy to pass the exam: Pass4itsure.com!
The latest Microsoft Windows Server 2012 70-411 pdf free download
[PDF] Free Microsoft 70-411 pdf dumps download from Google Drive: https://drive.google.com/open?id=1QeAw6CcjviOjYRyaptf9-r5F23WUDvQI
[PDF] Free Full Microsoft pdf dumps download from Google Drive: https://drive.google.com/open?id=1gdQrKIsiLyDEsZ24FxsyukNPYmpSUDDO
Valid information provided by Microsoft officials
Exam 70-411: Administering Windows Server 2012 – Microsoft: https://www.microsoft.com/en-us/learning/exam-70-411.aspx
This exam is part two of a series of three exams that test the skills and knowledge necessary to administer a Windows Server 2012
infrastructure in an enterprise environment. Passing this exam validates a candidate’s ability to administer the tasks required to
maintain a Windows Server 2012 infrastructure, such as user and group management, network access, and data security.
Passing this exam along with the other two exams confirms that a candidate has the skills and knowledge necessary for implementing,
managing, maintaining, and provisioning services and infrastructure in a Windows Server 2012 environment.
pass4itsure 70-411 exam Skills measured
This exam measures your ability to accomplish the technical tasks listed below. The percentages indicate the relative weight of each major topic area on the exam.
- Deploy, Manage, and Maintain Servers
- Configure File and Print Services
- Configure Network Services and Access
- Configure a Network Policy Server Infrastructure
- Configure and Manage Active Directory
- Configure and Manage Group Policy
Latest Microsoft Windows Server 2012 70-411 Exam Practice Test Questions and Answers
QUESTION 1
You have a server named Server1 that runs Windows Server 2012 R2. Server1 has the Remote Access server role
installed. On Server1, you create a network policy named Policy1.
You need to configure Policy1 to ensure that users are added to a VLAN.
Which attributes should you add to Policy1?
A. Tunnel-Tag, Tunnel-Password, Tunnel-Medium-Type, and Tunnel-Preference
B. Tunnel-Tag, Tunnel-Server-Auth-ID, Tunnel-Preference, and Tunnel-Pvt-Group-ID
C. Tunnel-Type, Tunnel-Tag, Tunnel-Medium-Type, and Tunnel-Pvt-Group-ID
D. Tunnel-Type, Tunnel-Password, Tunnel-Server-Auth-ID, and Tunnel-Pvt-Group-ID
Correct Answer: C
VLAN attributes used in network policy When you use network hardware, such as routers, switches, and access
controllers that support virtual local area networks (VLANs), you can configure Network Policy Server (NPS) network
policy to instruct the access servers to place members of Active Directory?groups on VLANs. Before configuring
network policy in NPS for VLANs, create groups of users in Active Directory Domain Services (AD DS) that you want to
assign to specific VLANs. Then when you run the New Network Policy wizard, add the Active Directory group as a
condition of the network policy. You can create a separate network policy for each group that you want to assign to a
VLAN. For more information, see Create a Group for a Network Policy. When you configure network policy for use with
VLANs, you must configure the RADIUS standard attributes Tunnel-Medium-Type, Tunnel-Pvt-Group-ID, and Tunnel-
Type. Some hardware vendors also require the use of the RADIUS standard attribute Tunnel-Tag. To configure these
attributes in a network policy, use the New Network Policy wizard to create a network policy. You can add the attributes
to the network policy settings while running the wizard or after you have successfully created a policy with the wizard.
Tunnel-Medium-Type. Select a value appropriate to the previous selections you made while running the New Network
Policy wizard. For example, if the network policy you are configuring is a wireless policy, in Attribute Value, select 802
(Includes all 802 media plus Ethernet canonical format). Tunnel-Pvt-Group-ID. Enter the integer that represents the
VLAN number to which group members will be assigned. For example, if you want to create a Sales VLAN for your
sales team by assigning team members to VLAN 4, type the number 4. Tunnel-Type. Select the value Virtual LANs
(VLAN). Tunnel-Tag. Some hardware devices do not require this attribute. If your hardware device requires this
attribute, obtain this value from your hardware documentation.
QUESTION 2
You have Windows Server 2012 R2 installation media that contains a file named Install.wim. You need to identify the
permissions of the mounted images in Install.wim.
What should you do?
A. Run dism.exe and specify the /get-mountedwiminfo parameter.
B. Run imagex.exe and specify the /verify parameter.
C. Run imagex.exe and specify the /ref parameter.
D. Run dism.exe and specify the/get-imageinfo parameter.
Correct Answer: A
/Get-MountedWimInfo Lists the images that are currently mounted and information about the mounted image such as
read/write permissions, mount location, mounted file path, and mounted image index.
References:
http: //technet. microsoft. com/en-us/library/cc749447(v=ws. 10). aspx
http: //technet. microsoft. com/en-us/library/dd744382(v=ws. 10). aspx
http://technet.microsoft.com/en-us/library/hh825224.aspx
QUESTION 3
Your network contains two Active Directory forests named contoso.com and dev.contoso.com. The contoso.com forest
contains a domain controller named DC1. The dev.contoso.com forest contains a domain controller named DC2. Each
domain contains an organizational unit (OU) named OU1.
Dev.contoso.com has a Group Policy object (GPO) named GPO1. GPO1 contains 200 settings, including several
settings that have network paths. GPO1 is linked to OU1.
You need to copy GPO1 from dev.contoso.com to contoso.com. What should you do first on DC2?
A. From the Group Policy Management console, right-click GPO1 and select Copy.
B. Run the mtedit.exe command and specify the /Domaintcontoso.com /DC: DC 1 parameter.
C. Run the Save-NetGpocmdlet.
D. Run the Backup-Gpocmdlet.
Correct Answer: A
To copy a Group Policy object:
In the GPMC console tree, right-click the GPO that you want to copy, and then click Copy. To create a copy of the GPO
in the same domain as the source GPO, right-click Group Policy objects, click Paste, specify permissions for the new
GPO in the Copy GPO box, and then click OK.
For copy operations to another domain, you may need to specify a migration table.
The Migration Table Editor (MTE) is provided with Group Policy Management Console (GPMC) to facilitate the editing of
migration tables. Migration tables are used for copying or importing Group Policy objects (GPOs) from one domain to
another, in cases where the GPOs include domain-specific information that must be updated during copy or import.
Source WS2008R2: Backup the existing GPOs from the GPMC, you need to ensure that the “Group Policy Objects”
container
is selected for the “Backup Up All” option to be available.
Copy a Group Policy Object with the Group Policy Management Console (GPMC) You can copy a Group Policy object
(GPO) either by using the drag-and-drop method or right-click method.
Applies To: Windows 8, Windows Server 2008 R2, Windows Server 2012
References:
http://technet.microsoft.com/en-us/library/cc785343(v=WS.10).aspx http://technet.microsoft.com/en-us/library/cc733107.aspx
QUESTION 4
Your network contains an Active Directory domain named contoso.com. Domain controllers run either Windows Server
2008, Windows Server 2008 R2, or Windows Server 2012 R2.
You have a Password Settings object (PSOs) named PSO1.
You need to view the settings of PSO1.
Which tool should you use?
A. Get-ADDefaultDomainPasswordPolicy
B. Active Directory Administrative Center
C. Local Security Policy
D. Get-ADAccountResultantPasswordReplicationPolicy
Correct Answer: B
In Windows Server 2012, fine-grained password policy management is made much easier than Windows Server
2008/2008 R2. Windows Administrators not have to use ADSI Edit and configure complicated settings to create the
Password Settings Object (PSO) in the Password Settings Container. Instead we can configure fine-grained password
policy directly in Active Directory Administrative Center (ADAC).
QUESTION 5
Your network contains an Active Directory domain named contoso.com. The domain contains a domain controller
named DC1 that runs Windows Server 2012 R2. DC1 is backed up daily.
The domain has the Active Directory Recycle Bin enabled.
During routine maintenance, you delete 500 inactive user accounts and 100 inactive groups. One of the deleted groups
is named Group1. Some of the deleted user accounts are members of some of the deleted groups.
For documentation purposes, you must provide a list of the members of Group1 before the group was deleted.
You need to identify the names of the users who were members of Group1 prior to its deletion.
You want to achieve this goal by using the minimum amount of administrative effort.
What should you do first?
A. Mount the most recent Active Directory backup.
B. Reactivate the tombstone of Group1.
C. Perform an authoritative restore of Group1.
D. Use the Recycle Bin to restore Group1.
Correct Answer: A
The Active Directory Recycle Bin does not have the ability to track simple changes to objects.
If the object itself is not deleted, no element is moved to the Recycle Bin for possible recovery in the future. In other
words, there is no rollback capacity for changes to object properties, or, in other words, to the values of these
properties.
QUESTION 6
Your network contains an Active Directory domain named contoso.com.
All user accounts reside in an organizational unit (OU) named OU1.
You create a Group Policy object (GPO) named GPO1. You link GPO1 to OU1. You configure the Group Policy
preference of GPO1 to add a shortcut named Link1 to the desktop of each user.
You discover that when a user deletes Link1, the shortcut is removed permanently from the desktop.
You need to ensure that if a user deletes Link1, the shortcut is added to the desktop again.
What should you do?
A. Enforce GPO1.
B. Modify the Link1 shortcut preference of GPO1.
C. Enable loopback processing in GPO1.
D. Modify the Security Filtering settings of GPO1.
Correct Answer: B
Replace Delete and recreate a shortcut for computers or users. The net result of the Replace action is to overwrite the
existing shortcut. If the shortcut does not exist, then the Replace action creates a new shortcut. This type of preference
item provides a choice of four actions: Create, Replace, Update, and Delete. The behavior of the preference item varies
with the action selected and whether the shortcut already exists.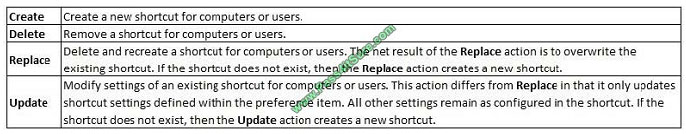
Refernces:
http://technet.microsoft.com/en-us/library/cc753580.aspx
http://technet.microsoft.com/en-us/library/cc753580.aspx
QUESTION 7
The domain contains 10 domain controllers and a read-only domain controller (RODC) named RODC01. All domain
controllers and RODCs are hosted on a Hyper-V host that runs Windows Server 2012 R2.
You need to identify whether deleted objects can be recovered from the Active Directory Recyle Bin.
Which cmdlet should you use?
A. Get-ADGroupMember
B. Get-ADDomainControllerPasswordReplicationPolicy
C. Get-ADDomainControllerPasswordReplicationPolicyUsage
D. Get-ADDomain
E. Get-ADOptionalFeature
F. Get-ADAccountAuthorizationGroup
G. Get-ADAuthenticationpolicySilo
H. Get-ADAuthenticationpolicy
Correct Answer: E
QUESTION 8
You have a server named Server1 that runs Windows Server 2012 R2. Server1 has the File Server Resource Manager
role service installed.
Each time a user receives an access-denied message after attempting to access a folder on Server1, an email
notification is sent to a distribution list named DL1.
You create a folder named Folder1 on Server1, and then you configure custom NTFS permissions for Folder1.
You need to ensure that when a user receives an access-denied message while attempting to access Folder1, an email
notification is sent to a distribution list named DL2. The solution must not prevent DL1 from receiving notifications about
other access-denied messages. What should you do?
A. From Server Manager, run the New Share Wizard to create a share for Folder1 by selecting the SMB Share –
Advanced option.
B. From the File Server Resource Manager console, modify the Access-Denied Assistance settings.
C. From the File Server Resource Manager console, modify the Email Notifications settings.
D. From Server Manager, run the New Share Wizard to create a share for Folder1 by selecting the SMB Share
-Applications option.
Correct Answer: A
Reference: http://technet.microsoft.com/en-us/library/jj574182.aspx#BKMK_12 When using the email model each of the
file shares, you can determine whether access requests to each file share will be received by the administrator, a
distribution list that represents the file share owners, or both.
The owner distribution list is configured by using the SMB Share ?Advanced file share profile in the New Share Wizard
in Server Manager.
QUESTION 9
Your network contains an Active Directory domain named contoso.com. All domain controllers run Windows Server
2012 R2. The domain contains 500 client computers that run Windows 8 Enterprise.
You implement a Group Policy central store.
You have an application named App1. App1 requires that a custom registry setting be deployed to all of the computers.
You need to deploy the custom registry setting. The solution must minimize administrator effort.
What should you configure in a Group Policy object (GPO)?
A. The Software Installation settings
B. The Administrative Templates
C. An application control policy
D. The Group Policy preferences
Correct Answer: D
Open the Group Policy Management Console. Right-click the Group Policy object (GPO) that should contain the new
preference item, and then click Edit. In the console tree under Computer Configuration or User Configuration, expand
the Preferences folder, and then expand the Windows Settings folder. Right-click the Registry node, point to New, and
select Registry Item. Group Policy preferences provide the means to simplify deployment and standardize
configurations. They add to Group Policy a centralized system for deploying preferences (that is, settings that users can
change later).
You can also use Group Policy preferences to configure applications that are not Group Policy-aware. By using Group
Policy preferences, you can change or delete almost any registry setting, file or folder, shortcut, and more. You are not
limited by the contents of Administrative Template files. The Group Policy Management Editor (GPME) includes Group
Policy preferences.
References:
http://technet.microsoft.com/en-us/library/gg699429.aspx
http: //www. unidesk. com/blog/gpos-set-custom-registry-
entries-virtual-desktops-disabling- machine-password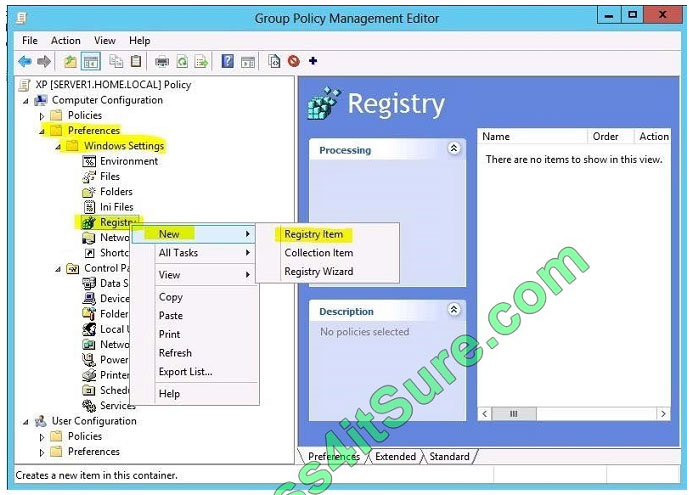
QUESTION 10
Your network contains an Active Directory domain named contoso.com. All domain controllers run Windows Server
2012 R2. The domain contains 500 client computers that run Windows 8.1 Enterprise and Microsoft Office 2013.
You implement a Group Policy central store.
You need to modify the default Microsoft Office 2013 Save As location for all client computers. The solution must
minimize administrative effort.
What should you configure in a Group Policy object (GPO)?
A. The Group Policy preferences
B. An application control policy
C. The Administrative Templates
D. The Software Installation settings
Correct Answer: A
Group Policy preferences provide the means to simplify deployment and standardize configurations. They add to Group
Policy a centralized system for deploying preferences (that is, settings that users can change later). You can also use
Group Policy preferences to configure applications that are not Group Policy-aware. By using Group Policy preferences,
you can change or delete almost any registry setting, file or folder, shortcut, and more. You are not limited by the
contents of Administrative Template files.
Reference: http://technet.microsoft.com/en-us/library/dn581922.aspx
QUESTION 11
Your network contains an Active Directory domain named contoso.com. All domain controllers run Windows Server
2012 R2.
In a remote site, a support technician installs a server named DC10 that runs Windows Server 2012 R2. DC10 is
currently a member of a workgroup.
You plan to promote DC10 to a read-only domain controller (RODC).
You need to ensure that a user named Contoso\User1 can promote DC10 to a RODC in the contoso.com domain. The
solution must minimize the number of permissions assigned to User1.
What should you do?
A. From Active Directory Users and Computers, run the Delegation of Control Wizard on the contoso.com domain
object.
B. From Active Directory Administrative Center, pre-create an RODC computer account.
C. From Ntdsutil, run the local roles command.
D. Join DC10 to the domain. Run dsmod and specify the /server switch.
Correct Answer: B
A staged read only domain controller (RODC) installation works in two discrete phases:
1.
Staging an unoccupied computer account
2.
Attaching an RODC to that account during promotion Reference: Install a Windows Server 2012 R2 Active Directory
Read-Only Domain Controller (RODC)
QUESTION 12
Your network contains four Network Policy Server (NPS) servers named Server1, Server2, Servers, and Server4.
Server1 is configured as a RADIUS proxy that forwards connection requests to a remote RADIUS server group named
Group1.
You need to ensure that Server2 and Server3 receive connection requests. Server4 must only receive connection
requests if both Server2 and Server3 are unavailable.
How should you configure Group1?
A. Change the Weight of Server4 to 10.
B. Change the Weight of Server2 and Server3 to 10.
C. Change the Priority of Server2 and Server3 to 10.
D. Change the Priority of Server4 to 10.
Correct Answer: D
During the NPS proxy configuration process, you can create remote RADIUS server groups and then add RADIUS
servers to each group. To configure load balancing, you must have more than one RADIUS server per remote RADIUS
server group. While adding group members, or after creating a RADIUS server as a group member, you can access the
Add RADIUS server dialog box to configure the following items on the Load Balancing tab:
Priority. Priority specifies the order of importance of the RADIUS server to the NPS proxy server. Priority level must be
assigned a value that is an integer, such as 1, 2, or 3. The lower the number, the higher priority the NPS proxy gives to
the RADIUS server. For example, if the RADIUS server is assigned the highest priority of 1, the NPS proxy sends
connection requests to the RADIUS server first; if servers with priority 1 are not available, NPS then sends connection
requests to RADIUS servers with priority 2, and so on. You can assign the same priority to multiple RADIUS servers,
and then use the Weight setting to load balance between them. Weight. NPS uses this Weight setting to determine how
many connection requests to send to each group member when the group members have the same priority level.
Weight setting must be assigned a value between 1 and 100, and the value represents a percentage of 100 percent. For
example, if the remote RADIUS server group contains two members that both have a priority level of 1 and a weight
rating of 50, the NPS proxy forwards 50 percent of the connection requests to each RADIUS server.
Advanced settings. These failover settingsprovide a way for NPS to determine whether the remote RADIUS server is
unavailable. If NPS determines that a RADIUS server is unavailable, it can start sending connection requests to other
group members. With these settings you can configure the number of seconds that the NPS proxy waits for a response
from the RADIUS server before it considers the request dropped; the maximum number of dropped requests before the
NPS proxy identifies the RADIUS server as unavailable; and the number of seconds that can elapse between requests
before the NPS proxy identifies the RADIUS server as unavailable.
The default priority is 1 and can be changed from 1 to 65535. So changing server 2 and 3 to priority 10 is not the way to go.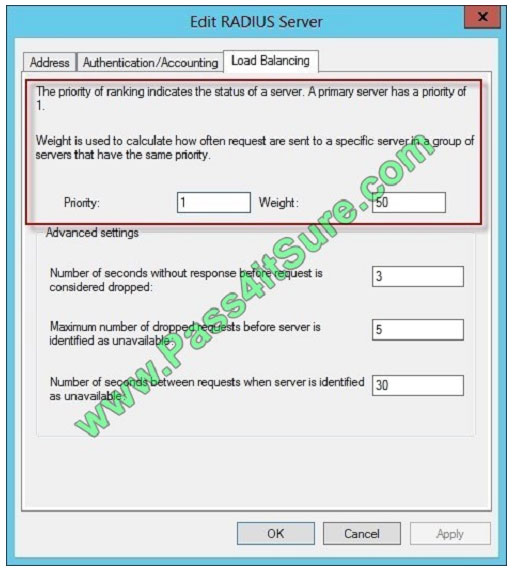
Reference: http: //technet. microsoft. com/en-us/library/dd197433(WS. 10). aspx
QUESTION 13
Your network contains an Active Directory forest named contoso.com. The functional level of the forest is Windows
Server 2008 R2.
All of the user accounts in the marketing department are members of a group named Contoso\MarketingUsers. All of the
computer accounts in the marketing department are members of a group named Contoso\MarketingComputers.
A domain user named User1 is a member of the Contoso\MarketingUsers group. A computer named Computer1 is a
member of the Contoso\MarketingComputers group.
You have five Password Settings objects (PSOs). The PSOs are defined as shown in the following table.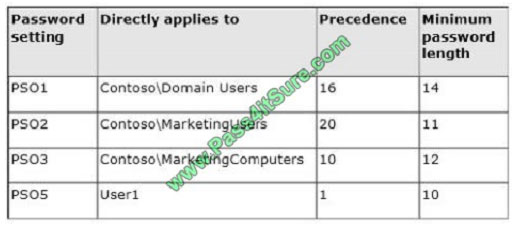
When User1 logs on to Computer1 and attempts to change her password, she receives an error message indicating that
her password is too short.
You need to tell User1 what her minimum password length is.
What should you tell User1?
A. 10
B. 11
C. 12
D. 14
Correct Answer: A
One PSO has a precedence value of 2 and the other PSO has a precedence value of 4. In this case, the PSO that has
the precedence value of 2 has a higher rank and, hence, is applied to the object.
Follow us! We update the latest effective exam dumps throughout the year to help you improve your skills! Microsoft Windows Server 2012 70-411 dumps share for free! Easy via 70-411 exam: https://www.pass4itsure.com/70-411.html (Q&As: 304)
Pass4itsure Promo Code 15% Off
Why Choose Pass4itsure?
Pass4itsure is the best provider of IT learning materials and the right choice for you to prepare for the Microsoft 70-411 exam. Other brands started earlier, but the price is relatively expensive and the questions are not the newest. Pass4itsure provides the latest real questions and answers with the lowest prices, help you pass the 70-411 exam easily at first try.