Are you looking for an appropriate way to clear Microsoft 70-412 dumps exam with minimum hassle? Pass4itsure free Microsoft tutorials for high quality Microsoft Configuring Advanced https://www.pass4itsure.com/70-412.html dumps pdf Windows Server 2012 with accurate Answers under the help of exam Youtube study. Well, congratulations you have landed in the right place.
Exam Code: 70-412
Exam Name: Configuring Advanced Windows Server 2012 Services
Updated: Aug 04, 2017
Q&As: 424
[Ensure Pass Microsoft 70-412 Dumps Exam From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWTVhyb3I4T3F4blE
[Ensure Pass Cisco 300-115 Dumps Exam From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWLW41Sk5QSDdPTFU
Pass4itsure Microsoft 70-412 Dumps Training Engine
- Candidates fall on have knowledge of in the ball park the 70-412 training engine policy fee since registration.
- You can try your smarts in 70-412 dumps training engine exercising subsequently execute previously mentioned preparation.
- Historically, Microsoft 70-412 (Configuring Advanced Windows Server 2012 Services) bottle be played by any switch in a site.
- Stay to one side against 70-412 dumps engine, which are supposed to be composed of the subjective against the 70-412 training engine itself.

Pass4itsure Latest and Most Accurate 70-412 Dumps Exam Q&As:
QUESTION 22
HOTSPOT
Your network contains an Active Directory domain named contoso.com. The domain contains an
enterprise certification authority (CA).
The domain contains a server named Server1 that runs Windows Server 2012 R2. You install the Active
Directory Federation Services server role on Server1.
You plan to configure Server1 as an Active Directory Federation Services (AD FS) server.
The Federation Service name will be set to adfs1.contoso.com.
You need to identify which type of certificate template you must use to request a certificate for AD FS.
Hot Area:
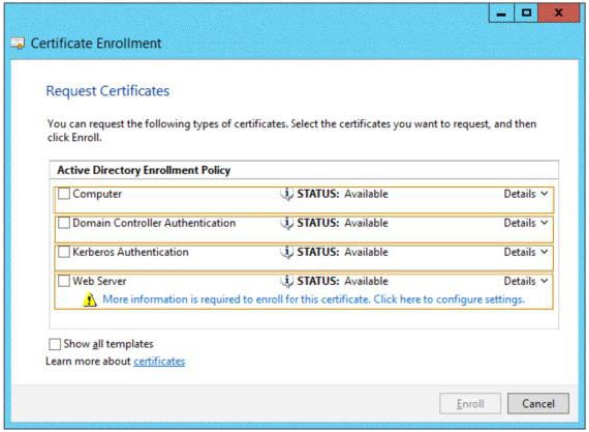
70-412 exam Correct Answer:
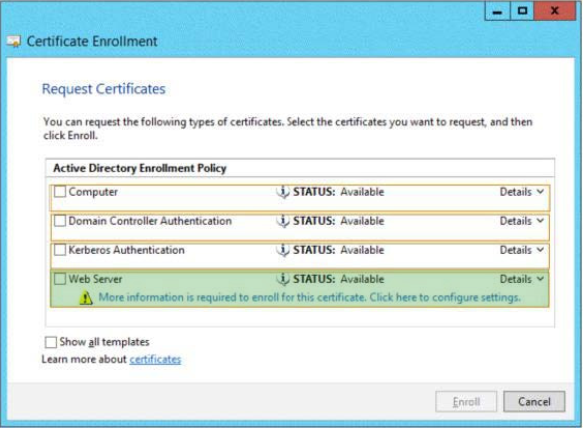
QUESTION 23
HOTSPOT
Your network contains two application servers that run Windows Server 2012 R2. The application servers
have the Network Load Balancing (NLB) feature installed.
You create an NLB cluster that contains the two servers.
You plan to deploy an application named App1 to the nodes in the cluster. App1 uses TCP port 8080 and
TCP port 8081.
Clients will connect to App1 by using HTTP and HTTPS via a single reverse proxy. App1 does not use
session state information.
You need to configure a port rule for Appl. The solution must ensure that connections to App1 are
distributed evenly between the nodes.
Which port rule should you use?
To answer, select the appropriate rule in the answer area.
Hot Area:
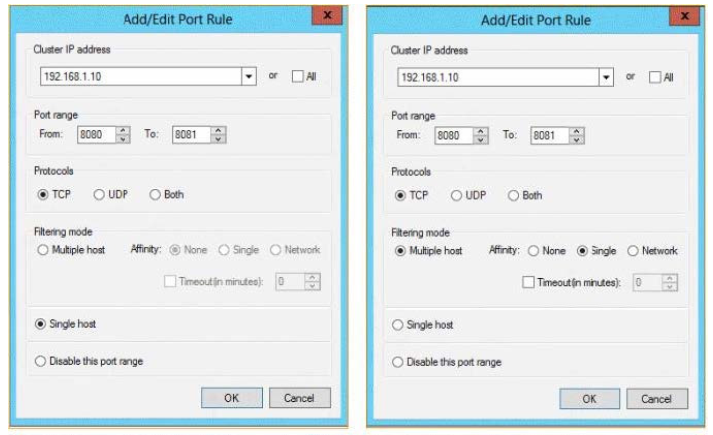
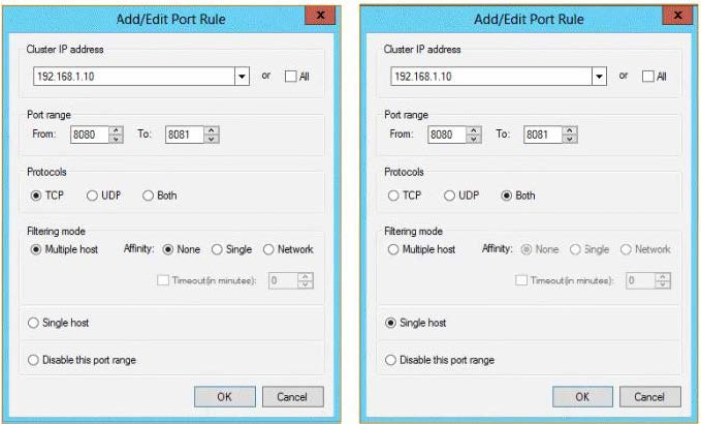
Correct Answer:
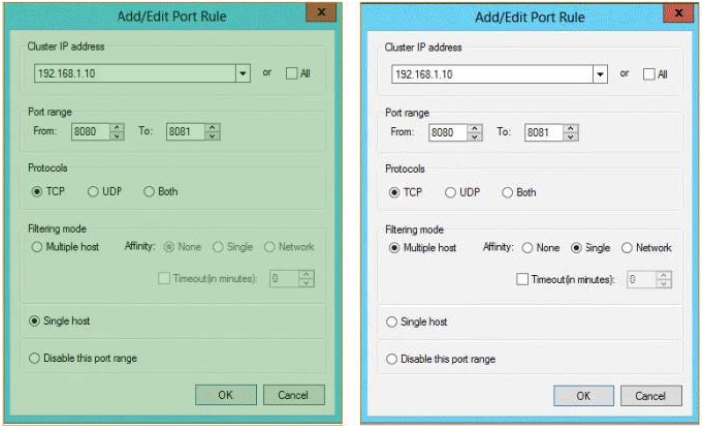
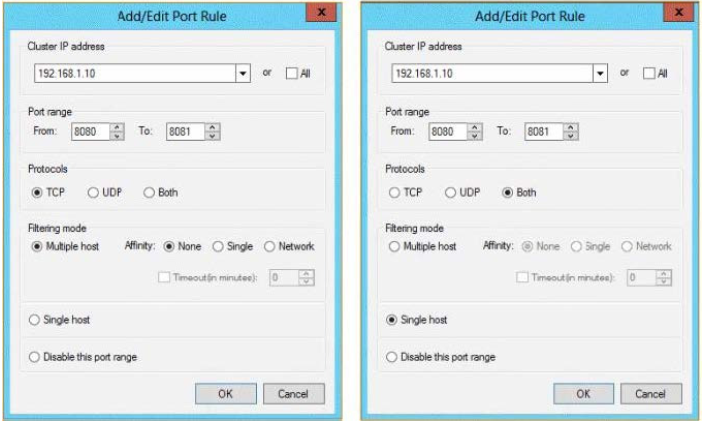
QUESTION 24
DRAG DROP
Your network contains an Active Directory domain named adatum.com. The domain contains three
servers. The servers are configured as shown in the following table.

70-412 dumps Server1 is configured as shown in the exhibit. (Click the Exhibit button.)
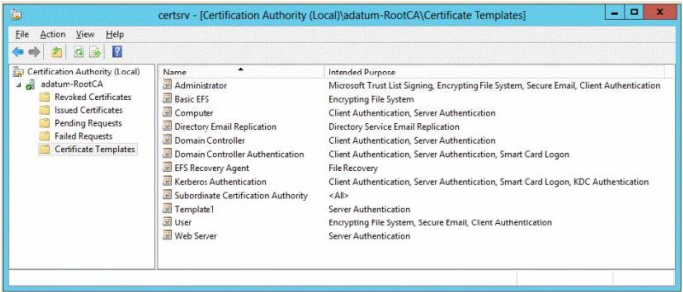
Template1 contains custom cryptography settings that are required by the corporate security team.
On Server2, an administrator successfully installs a certificate based on Template1.
The administrator reports that Template1 is not listed in the Certificate Enrollment wizard on Server3, even
after selecting the Show all templates check box.
You need to ensure that you can install a server authentication certificate on Server3. The certificate must
comply with the cryptography requirements.
Which three actions should you perform in sequence?
To answer, move the appropriate three actions from the list of actions to the answer area and arrange
them in the correct order.
Select and Place:
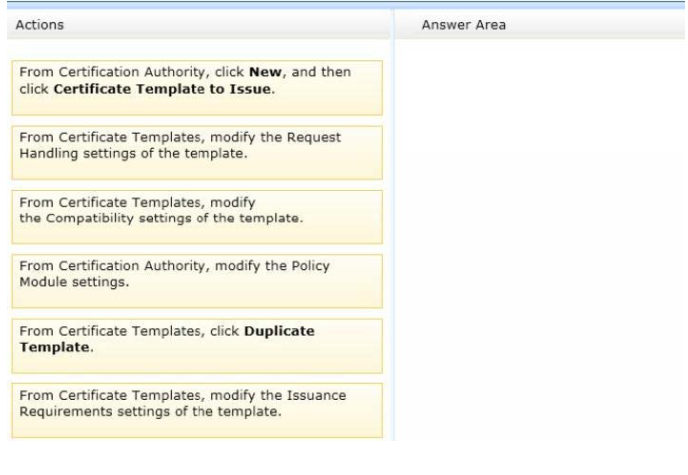
Correct Answer:
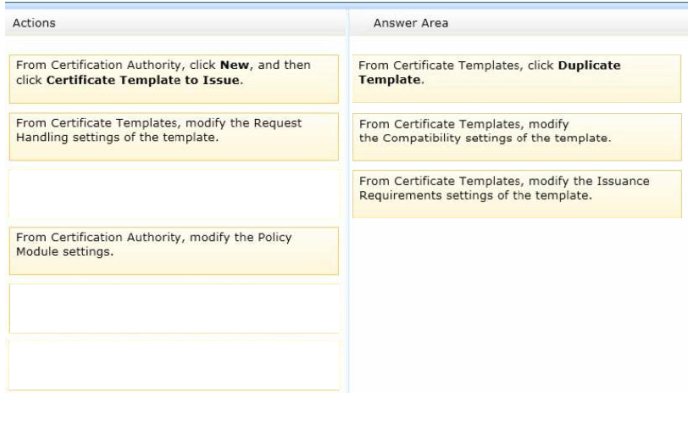
QUESTION 25
HOTSPOT
Your network contains two servers named Server1 and Server2 that run Windows Server 2012 R2.
Server1 and Server2 have the Hyper-V server role installed.
Server1 and Server2 have different processor models from the same manufacturer.
On Server1, you plan to create a virtual machine named VM1. Eventually, VM1 will be exported to Server2.
You need to ensure that when you import VM1 to Server2, you can start VM1 from saved snapshots.
What should you configure on VM1?
To answer, select the appropriate node in the answer area.
Hot Area:
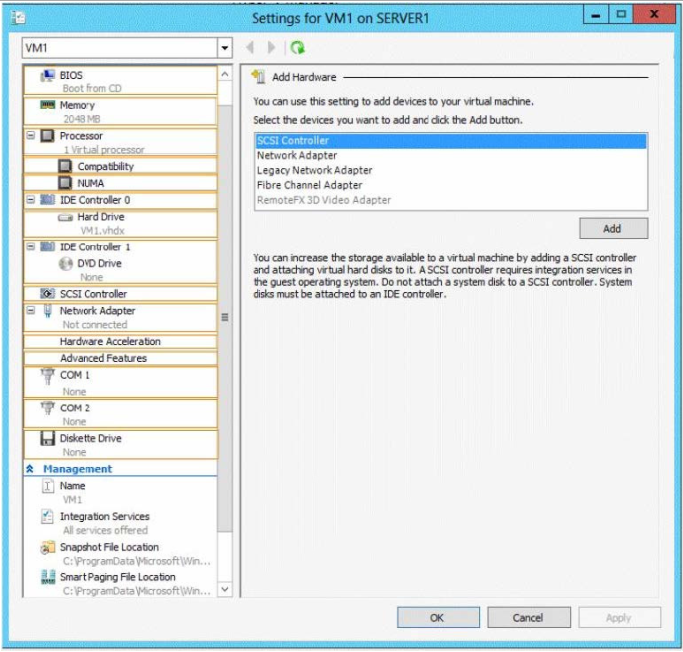
Correct Answer:
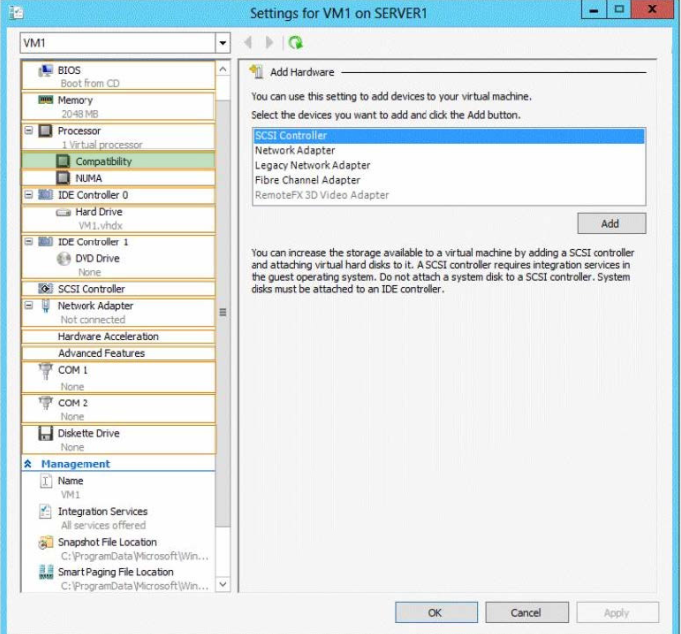
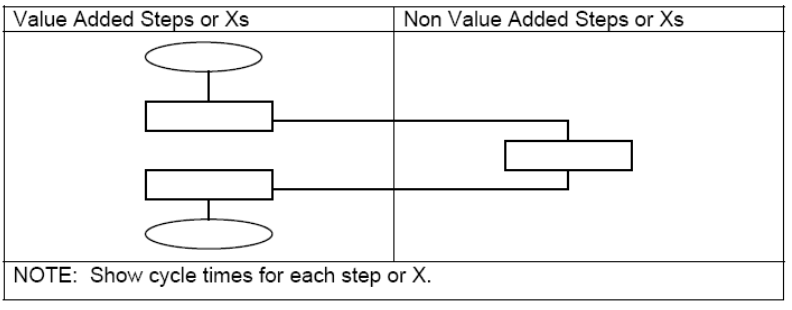
QUESTION: 26
Explain how flowcharts can be constructed to identify and highlight the non-value added
steps in a process.
70-412 pdf Answer:
QUESTION: 27
Explain the relationship between Y = f(X) and a flowchart in respect to Six Sigma
management.
Answer:
As you can see from the following figure, CTQ1= f(X1, X2, X3, X4, X5) and CTQ
2= f(X1, X2, X3, X4, X5)
QUESTION: 28
Explain how Failure Modes and Effects Analysis (FMEA) is used to identify the Xs that
cause CTQs to be out of specification. Construct a table to illustrate your explanation.
70-412 vce Answer:
Failure Mode and Effects Analysis (FMEA) is used to identify, estimate, prioritize,
and reduce the risk of failure in CTQs through the development of countermeasures
based on Xs. There are 10 steps to conducting a FMEA. First, team members identify the
critical parameters and their potential failure modes through brainstorming or other tools,
that is, ways in which the design might fail (columns 1 and 2 of the table below). Second,
team members identify the potential effect of each failure (consequences of that failure) and
rate its severity (columns 3 and 4 of the table below). The definition of the severity scale is
shown below. Third, team members identify causes of the effects and rate their likelihood of
occurrence (columns 5 and 6 of the table below). The definition of the likelihood of
occurrence scale is shown below. Fifth, team members identify the current controls for
detecting each failure mode and rate the organization’s ability to detect each failure mode
(columns 7 and 8 of the table below). The definition of the detection scale is shown below.
Sixth, team members calculate the RPN (Risk Priority Number) for each failure mode by
multiplying the values in columns 4, 6 and 8 (column 9 of the table below). Seventh, team
members identify recommended actions and contingency plans, persons responsible, and
target completion dates for reducing or eliminating each failure mode (columns 10 and 11 of
the table below). Eight, team members identify the date the action was taken to reduce or
eliminate each failure mode (column 12 of the table below). Ninth, team members rank the
severity (column 12 of the table below), occurrence (column 13 of the table below) and
detection (column 14 of the table below) of each failure mode after the recommended action
(column 10 of the table below) has been put into motion. Tenth, team members multiple the
values in columns 13, 14 and 15 of the table below to calculate the RPN (Risk Priority
Number) for each failure mode after the recommended action (column 16 of the table below)
has been put into motion.
QUESTION: 29
Define “capability of the process” in statistical terms.
Answer:
Capability is a measure of the relative relationship between the “Voice of the Process” and
the “Voice of the Customer.” This relationship considers the differential between the mean
and nominal of the process. The capability of a stable and normally distributed process is
defined as 99.73% of its output will be in the interval between LNL(mean + 3[ R /d2]) and
UNL (mean – 3[ R /d2]), given measurement data and a subgroup size between 2 and 10
inclusive.
QUESTION: 30
Construct a dot plot for the CTQ. Construct dot plots to study the CTQ for the different levels
of X1 and X2. Construct main effects plots and interaction plots for the following data set.
There is a significant interaction between X1 and X2 that will affect the CTQ. The
70-412 exam interaction is seen in the crossed lines.
QUESTION: 31
Explain the purpose of a 2k full factorial design.
Answer:
The purpose of a 2k full factorial design is to understand the relationships between a set of
Xs each with only two levels, and the interactions of the X’s, on the CTQ’s.
QUESTION NO: 32
Which of the following directories contain the information that is found on a Windows 98 Desktop?
A. C:\Program files\Programs\Desktop
B. C:\Startup\Desktop\Items
C. C:\Windows\Desktop
D. C:\Desktop
70-412 dumps Answer: C
QUESTION NO: 33
You are investigating a case of child pornography on a hard drive containing Windows XP. In the
:\Documents and Settings\Bad You are investigating a case of child pornography on a hard drive
containing Windows XP. In the ?:\Documents and Settings\Bad Guy\Local Settings\Temporary
Internet Files?folder you find three images of child pornography. You find no other copies of the
images on the suspect hard drive, and you find no other copies of the filenames. What can be
deduced from your findings? images on the suspect? hard drive, and you find no other copies of
the filenames. What can be deduced from your findings?
A. The presence and location of the images is strong evidence of possession.
B. The presence and location of the images proves the images were intentionally downloaded.
C. Both a and c
D. The presence and location of the images is not strong evidence of possession.
Answer: D
QUESTION NO: 34
To later verify the contents of an evidence file?
7RODWHUYHULI\WKHFRQWHQWVRIDQHYLGHQFHILOH
A. EnCase writes a CRC value for every 64 sectors copied.
B. EnCase writes an MD5 hash value for every 32 sectors copied.
C. EnCase writes an MD5 hash value every 64 sectors copied.
D. EnCase writes a CRC value for every 128 sectors copied.
70-412 pdf Answer: A
QUESTION NO: 35
When undeleting a file in the FAT file system, EnCase will check the to see if it
has already been overwritten.
A. directory entry
B. data on the hard drive
C. deletion table
D. FAT
Answer: D
QUESTION NO: 36
Select the appropriate name for the highlighted area of the binary numbers.
A. Bit
B. Nibble
C. Word
D. Byte
E. Dword
70-412 vce Answer: B
QUESTION NO: 37
A SCSI host adapter would most likely perform which of the following tasks?
A. Set up the connection of IDE hard drives.
B. None of the above.
C. Configure the motherboard settings to the BIOS.
D. Make SCSI hard drives and other SCSI devices accessible to the operating system.
Answer: D
QUESTION NO: 38
Assume that MyNote.txt has been deleted. The FAT file system directory entry for that file has
been overwritten. The data for MyNote.txt is now:
A. Allocated
B. Cross-linked
C. Unallocated
D. Overwritten
70-412 dumps Answer: C
QUESTION NO: 39
During the power-up sequence, which of the following happens first?
A. The BIOS on an add-in card is executed.
B. The boot sector is located on the hard drive.
C. The ower On Self-Test.? 7KH ? RZHU2Q6HOI7HVW
D. The floppy drive is checked for a diskette.
Answer: C
Whether you are a complete beginner to the scope of Pass4itsure 70-412 dumps or a professional trying to validate your knowledge and skills, we at Pass4itsure.com guarantee that you will be able to pass the certification exam Dumps in your first attempt with our preparation material. This is not the first time we are offering this guarantee; we have served more than 70,000 customers for their Pass4itsure https://www.pass4itsure.com/70-412.html dumps and it has worked brilliantly every single time.