
The preparation materials for Microsoft AZ-500 are generally lacking. Can anyone give advice on the exam? The basics are not to say, everyone knows to learn from the Microsoft Learn section. The secret to passing the exam is focused on the details, and the practice test is a huge help, reading all the answers and continuing to accept them until they pass. Pass4itSure AZ-500 exam dumps (Link https://www.pass4itsure.com/az-500.html) provide the most realistic AZ-500 practice test! All issues are verified and trustworthy.
For more Microsoft exam practice tests, stay tuned microsoft-technet.com blog!
Free Best Quality AZ-500 Exam Dumps PDF:
AZ-500 exam pdf free https://drive.google.com/file/d/16_DoJyg-HDQ_nNS1J3qiQiS0mSpJNMou/view?usp=sharing
Shared by Pass4itSure, part of the AZ-500 exam practice questions in the AZ-500 exam dumps PDF. Welcome to download and read, it will be helpful to your exam.
Latest Update Microsoft AZ-500 Exam Online Practice Test [Q1-Q15]
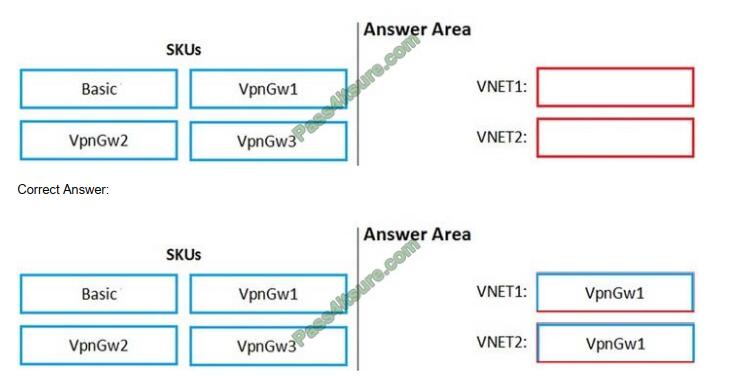
QUESTION 1
You are configuring network connectivity for two Azure virtual networks named VNET1 and VNET2.
You need to implement VPN gateways for the virtual networks to meet the following requirements:
1. VNET1 must have six site-to-site connections that use BGP.
2. VNET2 must have 12 site-to-site connections that use BGP.
3. Costs must be minimized.
Which VPN gateway SKU should you use for each virtual network? To answer, drag the appropriate SKUs to the correct
networks. Each SKU may be used once, more than once, or not at all. You may need to drag the split bar between
panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place:
QUESTION 2
You plan to use Azure Monitor Logs to collect logs from 200 servers that run Windows Server 2016.
You need to automate the deployment of the Log Analytics Agent to all the servers by using an Azure Resource
Manager template.
How should you complete the template? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:

Correct Answer:

QUESTION 3
SIMULATION
You need to create a web app named Intranet11597200 and enable users to authenticate to the web app by using
Azure Active Directory (Azure AD).
To complete this task, sign in to the Azure portal.
A. See the below.
Correct Answer: A
1. In the Azure portal, type App services in the search box and select App services from the search results.
2. Click the Create app service button to create a new app service.
3. In the Resource Group section, click the Create a new link to create a new resource group.
4. Give the resource group a name such as Intranet11597200RG and click OK.
5. In the Instance Details section, enter Intranet11597200 in the Name field.
6. In the Runtime stack field, select any runtime stack such as .NET Core 3.1.
7. Click the Review + create button.
8. Click the Create button to create the web app.
9. Click the Go to resource button to open the properties of the new web app.
10. In the Settings section, click on Authentication / Authorization.
11. Click the App Service Authentication slider to set it to On.
12. In the Action to take when the request is not authentication box, select Log in with Azure Active Directory.
13. Click Save to save the changes.
QUESTION 4
HOTSPOT
You have an Azure subscription that contains an Azure key vault named ContosoKey1.
You create users and assign them roles as shown in the following table.
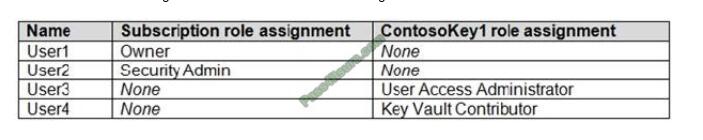
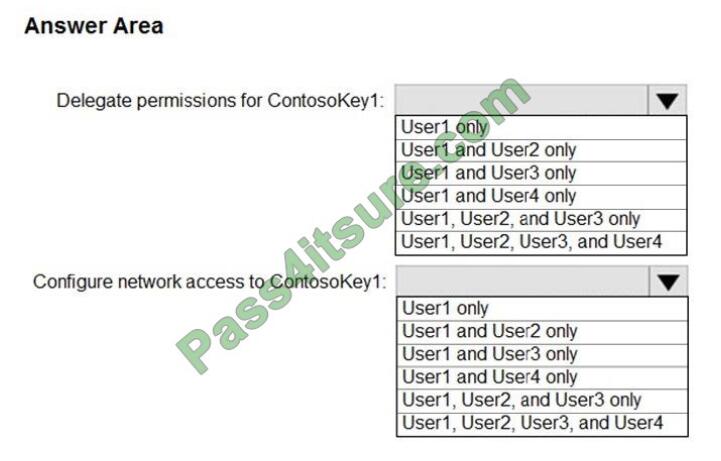
You need to identify which users can perform the following actions:
1. Delegate permissions for ContsosKey1.
2. Configure network access to ContosoKey1.
Which users should you identify? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Correct Answer:
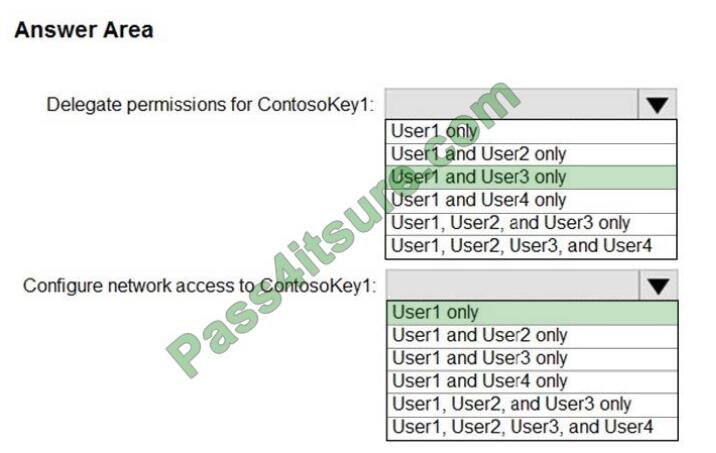
Reference: https://docs.microsoft.com/en-gb/azure/key-vault/general/rbac-guide
QUESTION 5
You have Azure Resource Manager templates that you use to deploy Azure virtual machines.
You need to disable unused Windows features automatically as instances of the virtual machines are provisioned.
What should you use?
A. device configuration policies in Microsoft Intune
B. an Azure Desired State Configuration (DSC) virtual machine extension
C. application security groups
D. Azure Logic Apps
E. security policies in Azure Security Center
F. device compliance policies in Microsoft Intune
Correct Answer: B
You can use Azure Automation State Configuration to manage Azure VMs (both Classic and Resource Manager), on-premises VMs, Linux machines, AWS VMs, and on-premises physical machines.
Note: Azure Automation State Configuration provides a DSC pull server similar to the Windows Feature DSC-Service so
that target nodes automatically receive configurations, conform to the desired state, and report back on their
compliance.
The built-in pull server in Azure Automation eliminates the need to set up and maintain your own pull
server. Azure Automation can target virtual or physical Windows or Linux machines, in the cloud or on-premises.
Reference: https://docs.microsoft.com/en-us/azure/automation/automation-dsc-getting-started
QUESTION 6
SIMULATION
You need to collect all the audit failure data from the security log of a virtual machine named VM1 to an Azure Storage
account. To complete this task, sign in to the Azure portal. This task might take several minutes to complete You can perform other tasks while the task completes.
A. See the below.
Correct Answer: A
Step 1: Create a workspace
Azure Monitor can collect data directly from your Azure virtual machines into a Log Analytics workspace for detailed
analysis and correlation.
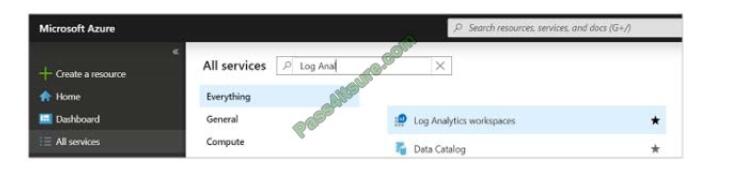
1. In the Azure portal, select All services. In the list of resources, type Log Analytics. As you begin typing, the list filters
based on your input. Select Log Analytics workspaces.
2. Select Create, and then select choices for the following items:
3. After providing the required information on the Log Analytics workspace pane, select OK.
While the information is verified and the workspace is created, you can track its progress under Notifications from the
menu.
Step 2: Enable the Log Analytics VM Extension
Installing the Log Analytics VM extension for Windows and Linux allows Azure Monitor to collect data from your Azure
VMs.
1. In the Azure portal, select All services found in the upper left-hand corner. In the list of resources, type Log Analytics.
As you begin typing, the list filters based on your input. Select Log Analytics workspaces.
2. In your list of Log Analytics workspaces, select DefaultWorkspace (the name you created in step 1).
3. On the left-hand menu, under Workspace Data Sources, select Virtual machines.
4. In the list of Virtual machines, select a virtual machine you want to install the agent on. Notice that the Log Analytics
connection status for the VM indicates that it is not connected.
5. In the details for your virtual machine, select Connect. The agent is automatically installed and configured for your Log Analytics workspace. This process takes a few minutes, during which time the Status shows Connecting.
After you install and connect the agent, the Log Analytics connection status will be updated with This workspace.
Reference: https://docs.microsoft.com/en-us/azure/azure-monitor/learn/quick-collect-azurevm
QUESTION 7
You have an Azure web app named webapp1.
You need to configure continuous deployment for webapp1 by using an Azure Repo.
What should you create first?
A. an Azure Application Insights service
B. an Azure DevOps organizations
C. an Azure Storage account
D. an Azure DevTest Labs lab
Correct Answer: B
To use Azure Repos, make sure your Azure DevOps organization is linked to your Azure subscription.
Reference: https://docs.microsoft.com/en-us/azure/app-service/deploy-continuous-deployment
QUESTION 8
You have an Azure subscription named Sub1 that is associated with an Azure Active Directory (Azure AD) tenant named
contoso.com. An administrator named Admin1 has access to the following identities:
1. An OpenID-enabled user account
2. A Hotmail account
3. An account in contoso.com
4. An account in an Azure AD tenant named fabrikam.com
You plan to use Azure Account Center to transfer the ownership of Sub1 to Admin1.
To which accounts can you transfer the ownership of Sub1?
A. contoso.com only
B. contoso.com, fabrikam.com, and Hotmail only
C. contoso.com and fabrikam.com only
D. contoso.com, fabrikam.com, Hotmail, and OpenID-enabled user account
Correct Answer: C
When you transfer billing ownership of your subscription to an account in another Azure AD tenant, you can move the
subscription to the new account\’s tenant.
If you do so, all users, groups, or service principals who had role-based access (RBAC) to manage subscriptions and their resources lose their access. Only the user in the new account who accepts your transfer request will have access to manage the resources.
Reference: https://docs.microsoft.com/en-us/azure/billing/billing-subscription-transfer
https://docs.microsoft.com/en-us/azure/billing/billing-subscription-transfer#transferring-subscription-to-an-account-inanother-azure-ad-tenant
QUESTION 9
HOTSPOT
You have an Azure subscription that contains a user named Admin1 and a resource group named RG1.
In Azure Monitor, you create the alert rules shown in the following table.
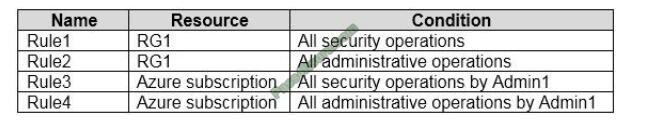
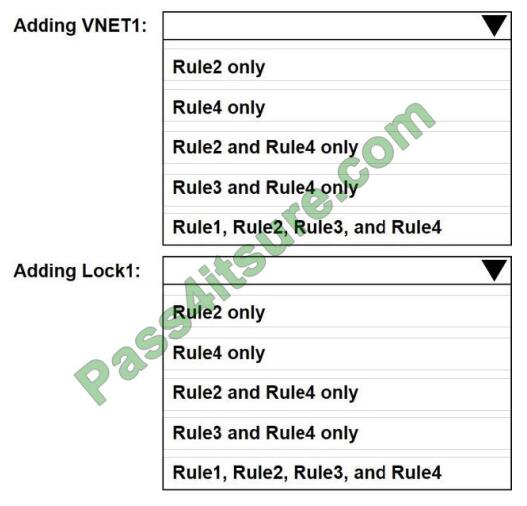
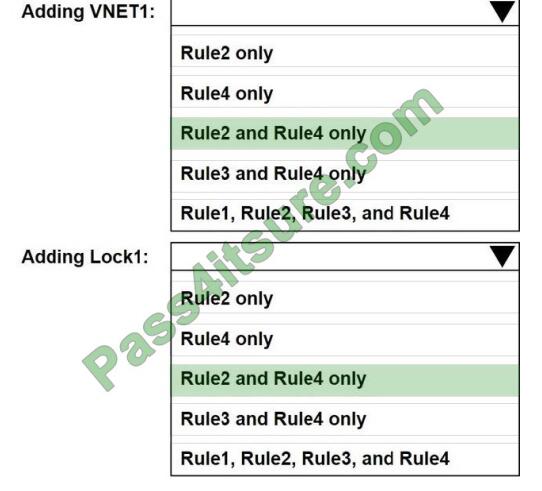
Admin1 performs the following actions on RG1:
1. Adds a virtual network named VNET1
2. Adds a Delete lock named Lock1
Which rules will trigger an alert as a result of the actions of Admin1? To answer, select the appropriate options in the
answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Correct Answer:
QUESTION 10
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains
a unique solution that might meet the stated goals. Some question sets might have more than one correct solution,
while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not
appear in the review screen.
You have an Azure Subscription. The subscription contains 50 virtual machines that run Windows Server 2012 R2 or
Windows Server 2016.
You need to deploy Microsoft Antimalware to virtual machines.
Solution: You add an extension to each virtual machine.
Does this meet the goal?
A. Yes
B. No
Correct Answer: A
You can use Visual Studio to enable and configure the Microsoft Antimalware service. This entails selecting Microsoft
Antimalware extension from the dropdown list under Installed Extensions and click Add to configure with default
antimalware configuration.
References: https://docs.microsoft.com/en-us/azure/security/fundamentals/antimalware
QUESTION 11
Your network contains an Active Directory forest named contoso.com. The forest contains a single domain.
You have an Azure subscription named Sub1 that is associated with an Azure Active Directory (Azure AD) tenant named
contoso.com.
You plan to deploy Azure AD Connect and to integrate Active Directory and the Azure AD tenant.
You need to recommend an integration solution that meets the following requirements:
1. Ensures that password policies and user login restrictions apply to user accounts that are synced to the tenant
2. Minimizes the number of servers required for the solution. Which authentication method should you include in the
recommendation?
A. federated identity with Active Directory Federation Services (AD FS)
B. password hash synchronization with seamless single sign-on (SSO)
C. pass-through authentication with seamless single sign-on (SSO)
Correct Answer: B
Password hash synchronization requires the least effort regarding deployment, maintenance, and infrastructure. This
level of effort typically applies to organizations that only need their users to sign in to Office 365, SaaS apps, and other
Azure AD-based resources. When turned on, password hash synchronization is part of the Azure AD Connect sync
process and runs every two minutes.
Incorrect Answers:
A: A federated authentication system relies on an external trusted system to authenticate users.
Some companies want to reuse their existing federated system investment with their Azure AD hybrid identity solution.
The maintenance and management of the federated system fall outside the control of Azure AD. It\’s up to the
organization by using the federated system to make sure it\’s deployed securely and can handle the authentication load.
C: For pass-through authentication, you need one or more (we recommend three) lightweight agents installed on
existing servers. These agents must have access to your on-premises Active Directory Domain Services, including your
on-premises AD domain controllers.
They need outbound access to the Internet and access to your domain controllers.
For this reason, it\’s not supported to deploy the agents in a perimeter network.
Pass-through Authentication requires unconstrained network access to domain controllers. All network traffic is
encrypted and limited to authentication requests.
References: https://docs.microsoft.com/en-us/azure/active-directory/hybrid/how-to-connect-pta
QUESTION 12
HOTSPOT
You have a file named File1.yaml that contains the following contents.
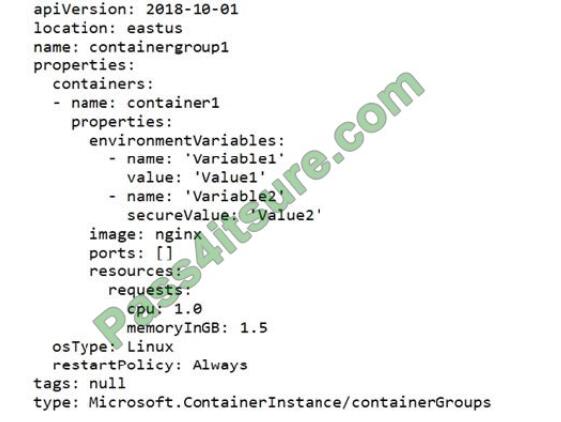
You create an Azure container instance named container1 by using File1.yaml.
You need to identify where you can access the values of Variable1 and Variable2.
What should you identify? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
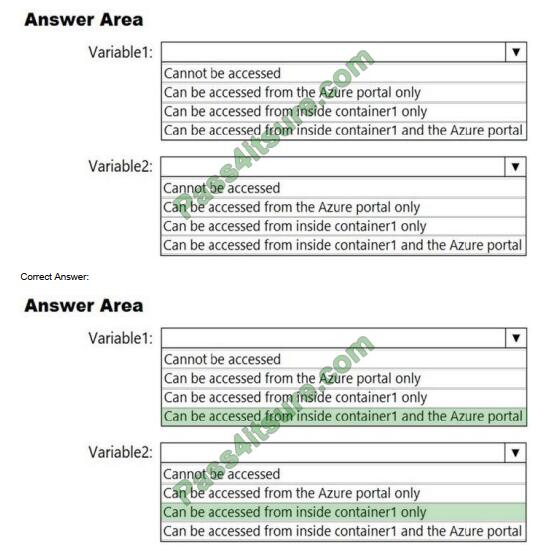
Reference: https://docs.microsoft.com/en-us/azure/container-instances/container-instances-environment-variables
QUESTION 13
You have an Azure subscription.
You enable Azure Active Directory (Azure AD) Privileged identify (PIM). Your company\\’s security policy for
administrator accounts have the following conditions:
1. The accounts must use multi-factor authentication (MFA).
2. The account must use 20-character complex passwords.
3. The passwords must be changed every 180 days.
4. The account must be managed by using PIM.
You receive alerts about administrators who have not changed their passwords during the last 90 days. You need to
minimize the number of generated alerts. Which PIM alert should you modify?
A. Roles don\\’t require multi-factor authentication for activation.
B. Administrator aren\\’t using their privileged roles
C. Roles are being assigned outside of Privileged identity management
D. Potential stale accounts in a privileged role.
Correct Answer: D
QUESTION 14
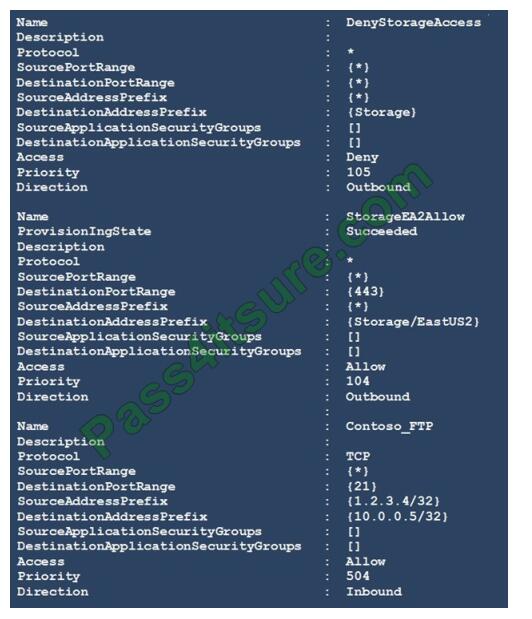
You have a network security group (NSG) bound to an Azure subnet.
You run Get-AzureRmNetworkSecurityRuleConfig and receive the output shown in the following exhibit.
Use the drop-down menus to select the answer choice that completes each statement based on the information
presented in the graphic. NOTE: Each correct selection is worth one point.
Hot Area:

Box 1: able to connect to East US 2
The StorageEA2Allow has DestinationAddressPrefix {Storage/EastUS2}
Box 2: allowed
TCP Port 21 controls the FTP session. Contoso_FTP has SourceAddressPrefix {1.2.3.4/32} and
DestinationAddressPrefix {10.0.0.5/32}
Note:
The Get-AzureRmNetworkSecurityRuleConfig cmdlet gets a network security rule configuration for an Azure network
security group. Security rules in network security groups enable you to filter the type of network traffic that can flow in
and out of virtual network subnets and network interfaces.
Reference:
https://docs.microsoft.com/en-us/azure/virtual-network/manage-network-security-group
QUESTION 15
You have an Azure subscription named Sub1 that contains the Azure key vaults shown in the following table:
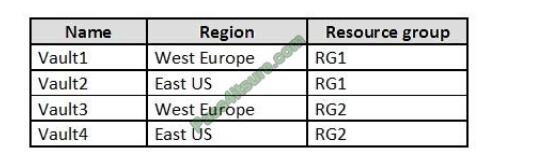
In Sub1, you create a virtual machine that has the following configurations:
1. Name: VM1
2. Size: DS2v2
3. Resource group: RG1
4. Region: West Europe
5. Operating system: Windows Server 2016
You plan to enable Azure Disk Encryption on VM1.
In which key vaults can you store the encryption key for VM1?
A. Vault1 or Vault3 only
B. Vault1, Vault2, Vault3, or Vault4
C. Vault1 only
D. Vault1 or Vault2 only
Correct Answer: A
In order to make sure the encryption secrets don\’t cross regional boundaries, Azure Disk Encryption needs the Key
Vault and the VMs to be co-located in the same region. Create and use a Key Vault that is in the same region as the VM
to be encrypted.
Reference: https://docs.microsoft.com/en-us/azure/security/azure-security-disk-encryption-prerequisites
Want to see more AZ-500 exam questions at Pass4itSure.
PS.
Pass4itSure AZ-500 exam dumps are the learning AZ-500 exam resource you’ve been looking for. Be careful in the exam, pay attention to the details, the AZ-500 exam success is near. Complete AZ-500 exam dumps question answers in this https://www.pass4itsure.com/az-500.html (Q-As: 320).
These suggestions, I hope they can be useful to you, come on!